 |
| Image Source |
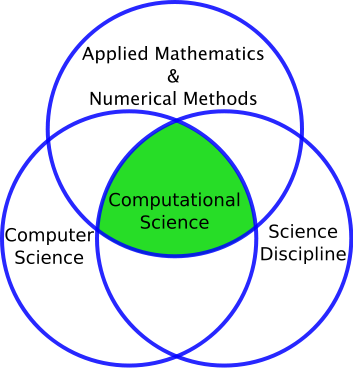
First of all what is computer science? Many people do not understand the complete meaning of this term. We often think that computer science is all about writing computer programs, developing software products and building computers. Well, this is not a complete story about Computer Science. Think about fields such as music and astronomy. Music is not just about creating musical instruments and astronomy is not just about building telescopes. Similarly, computer science is not just about tools of writing programs or building computers. It is about learning and using different tools. It is about providing resources to different researching fields. In fact, many of the researches in different fields are dependent upon the field of computer science.
For almost every scientific inventions and research, computer artifacts have become extremely helpful tool in each field. Scientific computing has allowed geologist to predict earthquakes, has allowed biologist to comprehend genetics, and has been very helpful in many other fields. Scientists often rely on computer methodology to do their research and make progresses in their respective fields. Such scientists are called computational scientists. For example, computational mathematician uses mathematics to research different theories and computational chemist uses chemistry to research different atomic models or molecular theory. Similarly, all scientists heavily are dependent upon the use of computers and computational processes.
This is what makes computer science makes more unique. It is the only field, which can make its own progress without depending upon other fields.
For almost every scientific inventions and research, computer artifacts have become extremely helpful tool in each field. Scientific computing has allowed geologist to predict earthquakes, has allowed biologist to comprehend genetics, and has been very helpful in many other fields. Scientists often rely on computer methodology to do their research and make progresses in their respective fields. Such scientists are called computational scientists. For example, computational mathematician uses mathematics to research different theories and computational chemist uses chemistry to research different atomic models or molecular theory. Similarly, all scientists heavily are dependent upon the use of computers and computational processes.
This is what makes computer science makes more unique. It is the only field, which can make its own progress without depending upon other fields.
Sources:
http://www.nitrd.gov/pitac/reports/20050609_computational/computational.pdf